Impinj Cryptographic Authentication
The Impinj Cryptographic Authentication feature uses a challenge-response protocol to verify a product’s authenticity with RAIN RFID, preventing counterfeits, ensuring consumer safety, and securing the supply chain.

Why use Impinj Cryptographic Authentication?
Counterfeit items erode a brand’s integrity, cost customers and retailers millions every year, and threaten consumer safety. A key component of the Impinj Authenticity solution engine, Impinj Cryptographic Authentication allows select Impinj tag chips programmed with unique cryptographic keys to enable secure authentication requests. With product authentication solutions powered by the Impinj platform, fake and gray market products such as counterfeit jewelry, handbags, shoes, and medications can be identified before they enter the supply chain.
Available on select Impinj RAIN RFID tag chips, Impinj Cryptographic Authentication:
- Fits seamlessly within existing inventory management, loss prevention, and supply chain processes
- Integrates with existing Impinj-enabled M700 series tag inlay designs and RAIN RFID readers
- Uses universal GS1 and ISO standards-based authentication methods that are supported by a broad vendor ecosystem
Industries that benefit from Impinj Cryptographic Authentication
 Combat counterfeits by quickly and automatically checking the authenticity of products in real-time
Combat counterfeits by quickly and automatically checking the authenticity of products in real-time
 Spot patterns in product movement and respond where counterfeit products enter
Spot patterns in product movement and respond where counterfeit products enter
 Prevent gray-market medications and devices that can lead to recalls, legal action, and erosion of consumer trust
Prevent gray-market medications and devices that can lead to recalls, legal action, and erosion of consumer trust
 Comply with regulations and minimize costs associated with returns, recalls, or counterfeits
Comply with regulations and minimize costs associated with returns, recalls, or counterfeits
.png?width=400&height=630&ext=.png) Protect consumer safety, ensure regulatory compliance, and avoid taxation loss by identifying bad products
Protect consumer safety, ensure regulatory compliance, and avoid taxation loss by identifying bad products

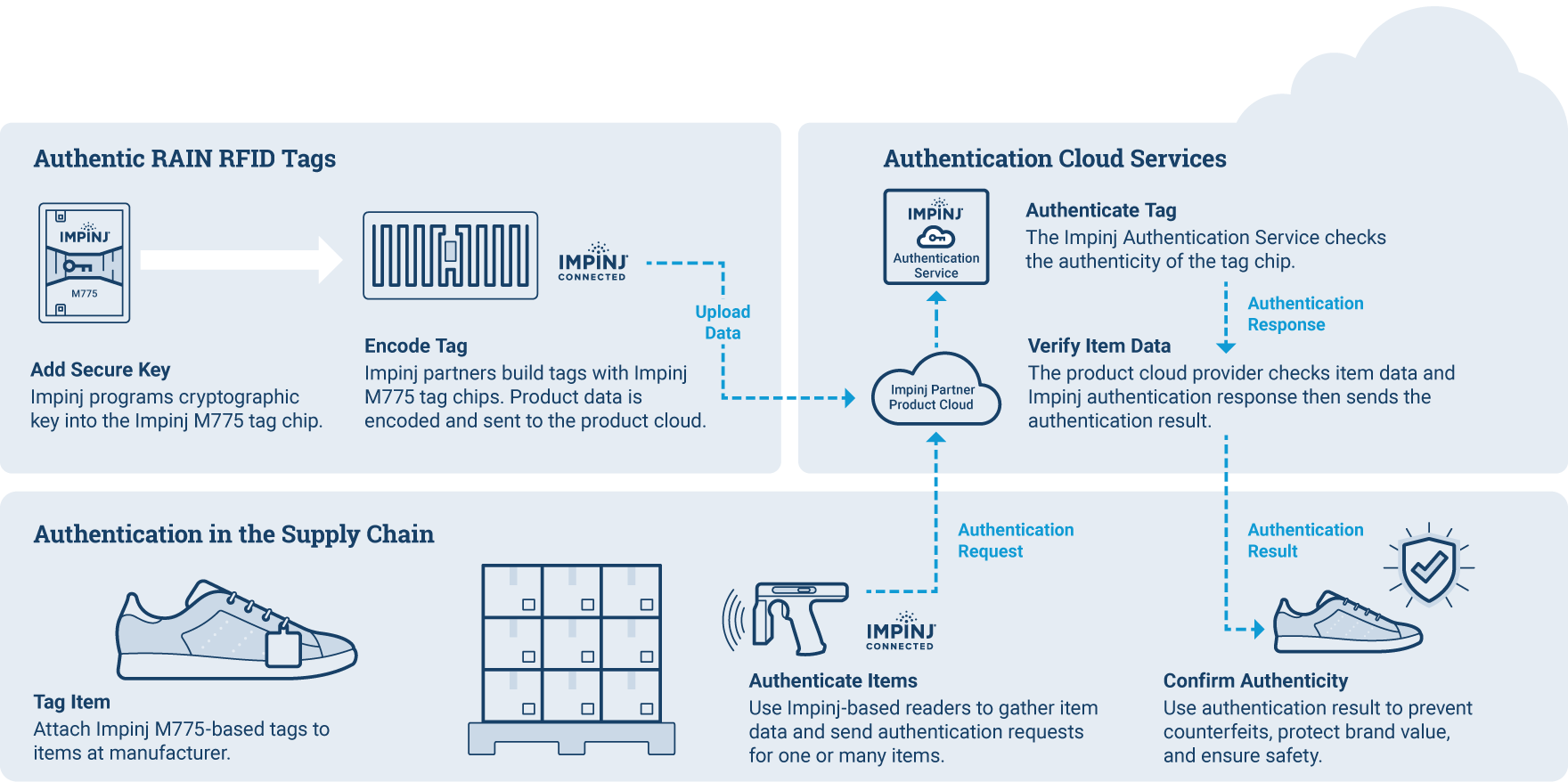
How Impinj Cryptographic Authentication works
Cryptographic authentication is a process that combines a cryptographic key and a cryptographic engine with an authentication request and response. Impinj Cryptographic Authentication uses the EPCglobal Gen2 standard, which means this capability can work with a range of RAIN RFID systems and devices. Here’s how it works:
- The cryptographic key is programmed into each Impinj M775 RAIN RFID tag chip at the factory.
- When a RAIN RFID reader sends the Gen2 Authenticate command to a tag, a cryptographic challenge-response protocol is used to test whether the valid key for a specific Tag ID is in the chip.
- The response is authenticated by the cloud-based Impinj Authentication Service, which sends the challenge result to the user and confirms the tag’s authenticity.
Visit the Impinj support site.
Compatible Impinj and partner products
Impinj-based product authentication solutions can be built using tags, inlays, and readers from Impinj and Impinj partners.

What is the Impinj Authenticity solution engine?
Impinj Cryptographic Authentication is an integral part of the Impinj Authenticity solution engine, which combines standards-based RAIN RFID and cryptography with tag chips, cloud services, readers, and partner products. The solution engine provides flexibility to cost-effectively add product authentication to shipping, inventory, point-of-sale, and other systems to authenticate goods along every step of the supply chain, from product manufacture through returns processing.
Support and Documentation
Read application notes and tips
Visit support portalLearn about the Impinj Authenticity Solution Engine
Visit support portalLearn about the Impinj Authentication Service
Visit support portal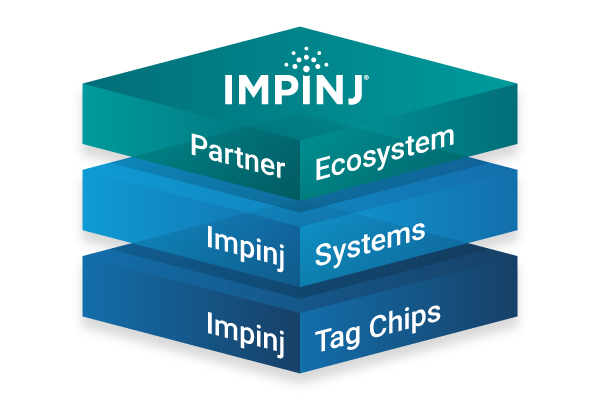
Impinj platform — a foundation for IoT solutions
The Impinj platform lays a foundation for IoT solutions development, extending the Internet’s reach from the cloud, through edge connectivity devices, all the way to physical items. Our broad partner ecosystem uses our platform's best-in-market products, capabilities, and technology to deliver whole products that address business needs. Wirelessly connect everyday items to discover, engage with, and protect them. Easy to deploy and use, our platform delivers performance unequaled by mix-and-match approaches built from other vendors’ products.