Impinj Authenticity Solution Engine
The Impinj Authenticity solution engine cryptographically authenticates products as genuine to prevent counterfeits, ensure product safety, and secure the supply chain.

Purpose-built for large scale product authentication solution development
The Impinj Authenticity™ solution engine provides flexibility to cost-effectively add product authentication to shipping, inventory, point-of-sale, and other systems to authenticate goods along every step of the supply chain, from manufacturing through shipping, customs, store inventory, point-of-sale, and returns processing.
Impinj partners can integrate the Impinj Authenticity solution engine with their current product offerings or develop robust solutions to meet the needs of enterprise customers and fit within existing operational processes, requiring minimal change management.
Using standards-based RAIN RFID and cryptography, the Impinj Authenticity solution engine combines new tag chips and cloud services with readers and partner products to enable streamlined enterprise IoT solution development.

AWARD-WINNING INNOVATION
Impinj Among Fast Company’s Most Innovative Companies
We are thrilled to be recognized by Fast Company for our Impinj Authenticity solution engine, which allows companies – from manufacturers to distributors– to verify that any individual item they make, transport, and sell is genuine.
The Impinj Authenticity solution engine powers product authentication
With Impinj RAIN RFID-based product authentication, individual items are tagged with RAIN RFID tags featuring the Impinj M775 tag chip, each of which is programmed with a unique cryptographic key. As items travel through the various stages of a supply chain, Impinj-enabled RAIN RFID readers read the tags and automatically verify them against a product database in the cloud. When they are identified early, counterfeit products can be prevented from reaching consumers.
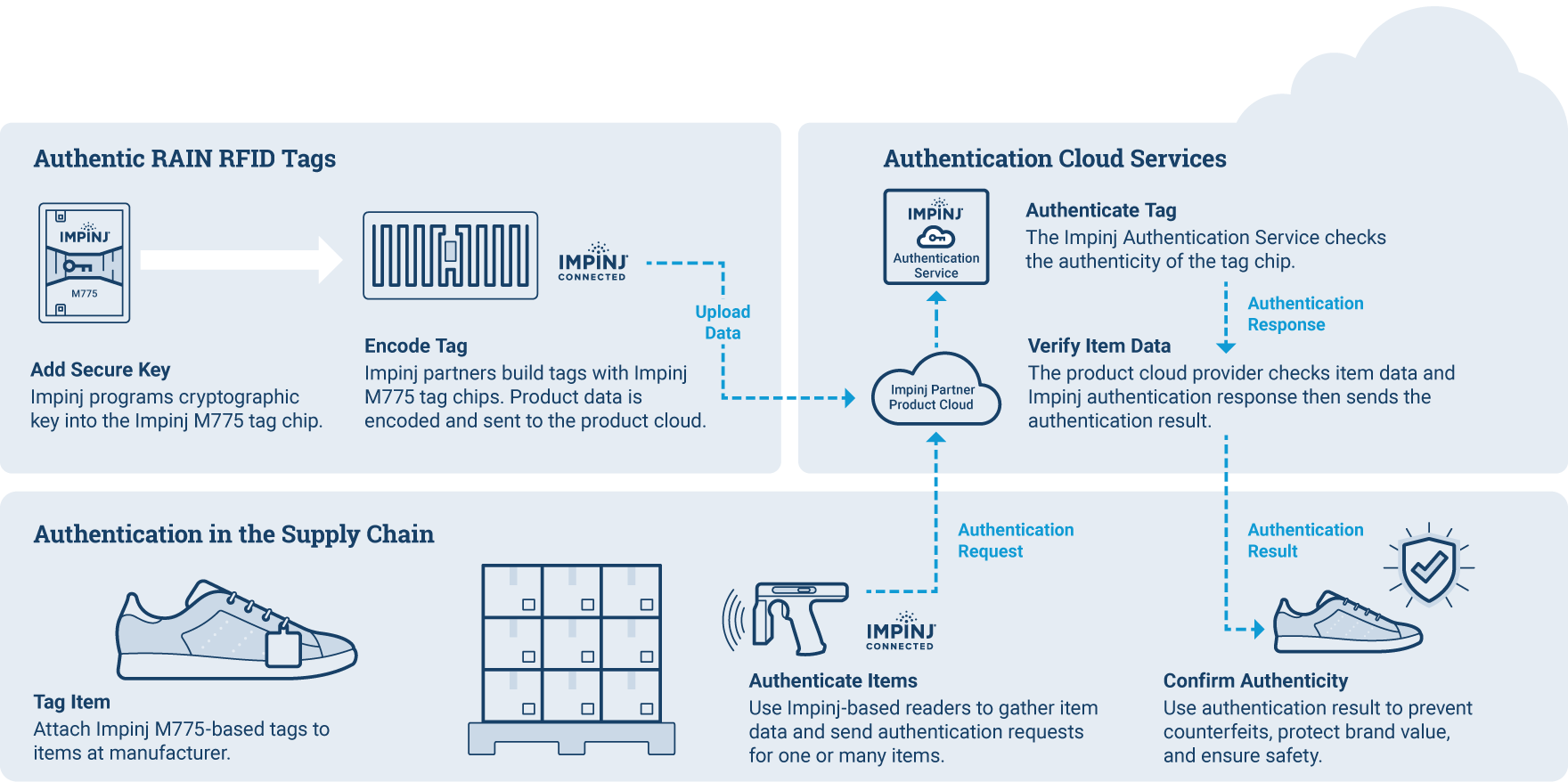
What is the Impinj Authenticity solution engine?
Designed for flexibility, Impinj partner solutions built on Impinj Authenticity can be deployed in a range of environments using fixed and mobile RAIN RFID readers in dock doors, forklifts, conveyers and carts, stock rooms, and staging areas. Select Impinj partners provide additional solution components, such as a product database that stores and verifies item data in the cloud.

Impinj M775 tag chip: Impinj tag partners build a variety of tags and inlays that can be attached to or embedded in nearly any item. Tags using Impinj M775 tag chips are programmed with unique cryptographic keys to enable secure authentication requests. These tag chips use a standards-based cryptographic method (ISO/IEC 29167) and respond to a GS1 Gen2-compliant reader command to provide secure authentication.
Impinj Authentication Service: This cloud-based Impinj service checks the authenticity of a tag and verifies item data with a partner or customer product database. The service provides secure access and manages all security-related processes to authenticate connected items, providing an API to interface with product cloud databases and enterprise applications.

Impinj R700 series readers, Impinj E family reader chips: Designed to deliver performance, reliability, security, and ease of use needed by enterprise deployments, Impinj-based RAIN RFID readers can scan hundreds of tags simultaneously and send authentication requests to tags as part of the authentication process. Impinj R700 series readers are designed for enterprise-grade IoT solutions. A wide range of RAIN RFID readers from Impinj partners built with Impinj E family reader chips can be integrated with Impinj Authenticity.

Select Impinj partners provide additional solution components, such as a product database that stores, retrieves, and verifies item data. Impinj partners, such as Avery Dennison Smartrac, Bluebird and Chainway, provide products that integrate with the Impinj Authenticity solution engine.
- Avery Dennison’s solution combines high-performance RAIN RFID inlays with the Impinj M775 chip and a robust and secure cloud platform through atma.io to properly retrieve, manage and verify unique item-level data.
- The new Bluebird RFR901 handheld reader and Chainway C66 handheld reader, powered by the Impinj E710 RAIN RFID reader chip, are enabled for use with Impinj M775-based tags as part of a product authentication solution.
Verify product authenticity in retail, supply chain and logistics, and healthcare
Learn More Retail
Protect high-value brands for fragrances, shoes, handbags, watches, and other items.
Supply Chain & Logistics
Combat gray markets by confirming the authenticity of products in the supply chain.
Healthcare
Protect patients from dangerous counterfeit medications, equipment, and devices.

Whitepaper
Learn how product authentication works at enterprise speed and scale
How exactly does product authentication work at scale? What are the challenges that companies face? What are the different authentication technologies? This white paper takes a deep dive into the world of product authentication; comparing platforms, outlining pros and cons, and explaining the technology in simple terms, charts, and graphics.
Impinj platform — a foundation for IoT solutions
The Impinj platform lays a foundation for IoT solutions development, extending the Internet’s reach from the cloud, through edge connectivity devices, all the way to physical items. Our broad partner ecosystem uses our platform's best-in-market products, capabilities, and technology to deliver whole products that address business needs. Wirelessly connect everyday items to discover, engage with, and protect them. Easy to deploy and use, our platform delivers performance unequaled by mix-and-match approaches built from other vendors’ products.
